WARNING: THIS ROUNDCUBE PLUGIN IS UNMAINTAINED !
DKIMSTATUS displays the status of the DKIM Signature of each email your read in Roundcube.
Package DkimStatus is included in Debian Wheezy and Ubuntu Precise via the package roundcube-plugins-extra. See roundcube-plugins-extra.
Download
LATEST (roundcube 0.8+): dkimstatus.zip
If you are using Roundcube < 0.8, you must use dkimstatus v0.4.8: dkimstatus-v0.4.8.tar
Description
DKIMSTATUS parses the results of the DKIM (or SPF) validation of a message. It requires that incoming emails are previously checked by a DKIM validation engine (such as dkimproxy). DKIMSTATUS displays the status of the DKIM signature of the message next to the 'From' field of the email.
A signature status can have one of the 4 following states:
- no signature information
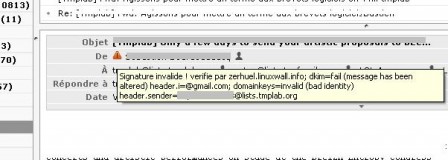
- invalid signature (most likely, the message has been modified after the signature has been applied)
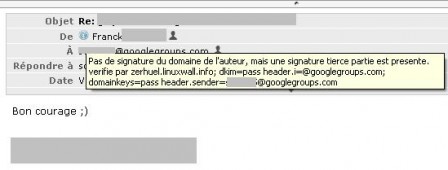
- valid signature from a 3rd party domain (ie. not the domain of the author)
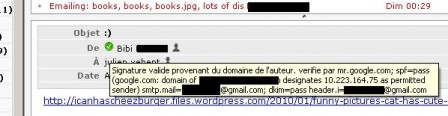
- valid signature from the domain of the author (the message can be trusted as coming from the author)
DKIMSTATUS has been tested and validated with DKIMproxy 0.3 beta 1 and Amavis 2.6.1 (both using Mail::DKIM perl module by Jason Long).
Version 0.9.5 tested against roundcube 0.9.5 Version 0.8.1 tested against roundcube 0.8 Version 0.4.8 tested against roundcube 0.6 & 0.7 Version 0.4.7 tested against roundcube 0.5.2 Version 0.4.6 tested against roundcube 0.5. Version 0.4.3 tested against roundcube 0.4. Version 0.4.2 tested against roundcube 0.3.
Changelog
- 0.9.5: Fixed author domain verification (ngpitt) & Add small fix if dkim and domainkey signature exists (saamich)
- 0.8.1: Rename imap_init hook into storage_init (Daniel Hahler)
- 0.4.8: Added X-Spam-Status for spamassassin (thanks Ashish Shukla for the patch)
- 0.4.7: added license information (GPLv2)
- 0.4.6: italian translation from Roberto Puzzanghera
- 0.4.5: updated german translation by Simon
- 0.4.4: japanese translation from Taka
- 0.4.3: from Sergio Cambra: SPF fix, image function and spanish translation
- 0.4.2 : added translations: Polish (thanks to Tomasz Chiliński), Romanian and German
Installation
Untar the archive in your plugins folder and add 'dkimstatus' to your list of activated plugins in Roundcube's main.inc.php config file.
// List of active plugins (in plugins/ directory)
$rcmail_config'plugins' = array('managesieve', 'vcard_attachments', 'dkimstatus');
Repository
Contact
julien { at } linuxwall.info
Screenshots
Valid signature from the author's domain
Third party signature
Invalid signature (due to mailing list manipulation, probably)




13 reactions
1 From Alexander - 28/06/2010, 14:20
DKIM check does not produce any header (see rfc4871).
"Authentication-results" header is described in the rfc5451.
This plugin wrong parse "Authentication-results" header.
2 From Julien Vehent - 11/08/2010, 12:01
Strictly speaking, yes, you are right. But the goal of this plugin is not to perform the DKIM validation, but to simply display it.
Therefore, it needs a information to rely on, and the Authentication-Result header is probably the most appropriate for that.
There is a number of improvements, such as parsing several consecutive Authentication-Results, that I would like to work on. If you have any request or comment, feel free to post them here.
3 From Daniel Hahler - 13/10/2010, 14:24
Thanks!
The installation paragraph should get fixed as follows though:
"Untar the archive in your plugins folder and add 'dkimstatus' to your list of activated plugins in Roundcube's main.inc.php config file."
("plugins" and "dkimstatus")
4 From Simon - 21/01/2011, 20:46
The german translation is, to tell the truth, very bad. I have corrected it and could send it to you, if you want. Just send me an e-mail!
5 From Georges - 11/02/2011, 10:29
Hello,
I've installed DKIMSTATUS, but it doesn't work for me.
Source extract of one e-mail :
(.....)
Return-Path: <p-rn2w8kwba4ajtd75rfdrvjlwgqtftct39re9mslkl99s4an4ppky982-1s2sb@newsletters.lefigaro.fr>
X-Original-To: xxxxxxx
Delivered-To: xxxxxxx
Received-SPF: pass (ks351886.kimsufi.com: domain of p-rn2w8kwba4ajtd75rfdrvjlwgqtftct39re9mslkl99s4an4ppky982-1S2SB@newsletters.lefigaro.fr designates 178.248.184.94 as permitted sender)
Received: from mta184094.g.emstechnology2.net (mta184094.g.emstechnology2.net [178.248.184.94])
by ks351886.kimsufi.com (Postfix) with ESMTP id 0F4A71668755
for <xxxxxxx>; Fri, 11 Feb 2011 10:12:27 +0100 (CET)
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=selector1; d=newsletters.lefigaro.fr;
h=From:Reply-To:To:Message-ID:Date:Subject:MIME-Version:Content-type:Content-Transfer-Encoding; i=publipostage@newsletters.lefigaro.fr;
bh=Bu+67cShowIhaxcNBN91r+uH0kw=;
b=wDQhxdBiOzV6xSVRXbM48F8XYLfD88h7lSdELru0s9GdQbS07UJqaz0raTHaVcq4v7JqsTnMJFVj
ugTVM66Buw==
DomainKey-Signature: a=rsa-sha1; c=nofws; q=dns; s=selector1; d=newsletters.lefigaro.fr;
b=hFDP3mSs3gikBRagvAKo//NgeW2rWVgDrLHRJ6VddhihVyVsB5ghcYgw9/b9YBVLhE6ku8+Ma4z+
zgXbFXdm+Q==;
Received: by mta184092.g.emstechnology2.net (PowerMTA(TM) v3.5r15sb2) id hajunm10vrk6 for <xxxxxxx>; Fri, 11 Feb 2011 10:12:27 +0100 (envelope-from <p-rn2w8kwba4ajtd75rfdrvjlwgqtftct39re9mslkl99s4an4ppky982-1S2SB@newsletters.lefigaro.fr>)
From: "Le Figaro.fr" <publipostage@newsletters.lefigaro.fr>
(.....)
.... and DKIMSTATUS says "status : unknown".
Where am I wrong ?
Thanks
6 From Julien Vehent - 11/02/2011, 16:54
Hi Georges,
It seems that you read the instructions a bit too fast. DKIMSTATUS does not verify DKIM signatures, it only display the result of the verification.
Quoting from above:
When incoming emails enter your mail server, you must control the DKIM signature using something like DKIMproxy. DKIMproxy will set two headers: Authentication-Results and X-DKIM-Authentication-Results. Those headers are checked by DKIMSTATUS to display the DKIM... status :)
7 From Georges - 13/02/2011, 17:45
Thank you Julien for your help.
So the line :
Received-SPF: pass (ks351886.kimsufi.com: domain of p-rn2w8kwba4ajtd75rfdrvjlwgqtftct39re9mslkl99s4an4ppky982-1S2SB@newsletters.lefigaro.fr designates 178.248.184.94 as permitted sender)
does not mean that my message has been checked by postfix?
8 From Julien Vehent - 13/02/2011, 19:24
@Georges :
I am not very familiar with the SPF syntax, but your headers seems to indicate that the signature how the message has been properly verified.
Does your message contain the "authentication-results" header ? DKIMstatus reads this header (and also "x-dkim-authentication-results") to determine the status of the signature, if it's missing, the plugin won't be able to display anything.
What component do you use to validate the SPF signature ? Does it set any additional header other than "Received-SPF" ?
Note: I've never tested DKIMstatus with SPF signatures, it might be a good opportunity to do it :)
9 From Georges - 14/02/2011, 08:59
@Julien : Currently, my Postfix is configured to check SPF signatures using Mail::SPF::Query (from CPAN) (see postfix-policyd-spf-perl package from openspf.org).
I've checked my headers, and I don't see any "authentication-results".
As an example, full headers of one message I received :
Return-Path: <dg7776-ovh@nichandle.ovh.net>
X-Original-To: xxx@yyy.com
Delivered-To: xxx@yyy.com
Received-SPF: pass (ks351886.kimsufi.com: domain of dg7776-ovh@nichandle.ovh.net designates 213.186.36.34 as permitted sender)
Received: from 5.mail-out.ovh.net (5.mail-out.ovh.net [213.186.36.34])
by ks351886.kimsufi.com (Postfix) with SMTP id A4B9616686F6
for <xxx@yyy.com>; Sun, 13 Feb 2011 12:42:35 +0100 (CET)
Received: (qmail 2733 invoked by uid 503); 13 Feb 2011 11:42:50 -0000
Received: from a2.ovh.net (HELO mozg.ha.ovh.net) (213.186.33.62)
by 5.mail-out.ovh.net with SMTP; 13 Feb 2011 11:42:50 -0000
Received: by mozg.ha.ovh.net (Postfix, from userid 500)
id A5C8817351; Sun, 13 Feb 2011 12:42:36 +0100 (CET)
Subject: =?ISO-8859-1?Q?Soci=E9t=E9=20Ovh=20:=20suivi=20de=20vos=20services=20-=20dg7776-ovh?=
X-Ovh-Template: relances/fr/followup.model
X-Ovh-Nic: dg7776-ovh
X-Ovh-Keywords: nic:dg7776-ovh
Mime-Version: 1.0
Content-Type: text/plain; charset=ISO-8859-1
To: xxx@yyy.com
Content-Transfer-Encoding: 8bit
X-Ovh-Section: renewals
From: support@ovh.com
Message-Id: <20110213114236.A5C8817351@mozg.ha.ovh.net>
Date: Sun, 13 Feb 2011 12:42:36 +0100 (CET)
X-Ovh-Tracer-Id: 14103585183243147006
X-Moninfor-MailScanner: Found to be clean
X-Moninfor-MailScanner-SpamCheck: not spam, SpamAssassin (not in cache,
score=0.379, required 6, AWL -0.21, BAYES_00 -2.60,
FH_DATE_PAST_20XX 3.19, SPF_PASS -0.00)
X-Moninfor-MailScanner-From: dg7776-ovh@nichandle.ovh.net
X-Moninfor-MailScanner-To: xxx@yyy.com
X-Spam-Status: No
@[Julien Vehent|#c2369] : @[Julien Vehent|#c2369] :
10 From Julien Vehent - 15/02/2011, 17:56
@Georges :
It seems that the guys at openspf.org wanted to use the authentication-results at some point
Concerning the Authentication-Results: header, Julian declared that he was strongly leaning towards making use of it for the SPF specification as the long-term successor of the custom Received-SPF: header, so as to avoid actively promoting two distinct headers with distinct formats.
source: http://www.openspf.org/Council_Meeting/2005-01-15
However, I couldn't find anything regarding this header on their website. Maybe you should ask on the mailing list.
The authentication-results header was defined to replace all of the other headers, and avoid having one header per technology. As stated in the RFC5451 :
I can't imagine that openspf.org did not implement it...
11 From Julien Vehent - 15/02/2011, 18:07
@Georges :
Humm... well, actually, it seems that Mail::SPF has not been updated since 2008, so they probably did not implement the header defined in a 2009 RFC.
You should consider using DKIMproxy, take a look at my article on how to implement it: french version, english version
12 From Anders Lind - 29/05/2011, 22:08
1. I would suggest also checking Received-SPF: Pass/Fail etc. (E.g. using a regular expression to check it. Some inspiration for dealing with the check: http://www.openspf.org/SPF_Received... )
I use tools for sender check postfix-policyd-spf-python and dkim-filter in Ubuntu 10.04/Lucid LTS - when going through solutions for SPF and DKIM their seems to be a lot so a lot of the users of your RC plugin will likely have different solutions for checking SPF and DKIM
. Forcing people to explicitly use dkimproxy might not be the optimal solution.
2. Perhaps show two icons one for DKIM and one for SPF.
3. Another idea would be some RC/DKIMSTATUS configuration option about checking SPF and DKIM on the fly when the message is opened in RC - for two(!) reasons:
A. Fake mail-headers from the sender of the mail/spam/junk/advertisement could then be caught.
B. People administering mail-servers might not check SPF and/or DKIM, which would make it beneficial for the (end) user to see whether a mail comes from the correct bank or is a fake attempt from a hacker/cracker/hijacker/phisher. This particular 'bank' example and inspiration for the on fly check I thought off when visiting: https://addons.mozilla.org/en-US/th... (try to inspect the images on the page.)
4. Another idea would be to state what the DKIM and SPF checks actually mean - like a small about icon with some tool-tip - e.g. "DKIM: whether mail was signed and verified by key check." and e.g. "SPF: whether mail originate from authorized server specified by DNS records." -
well authorized because we cannot authenticate with SPF as far as I know.
13 From Vincent-Xavier Jumel - 24/02/2012, 20:38
Hi,
I've got several mails which contains
Authentication-Results: mail.thetys-retz.net; x-dkim-rep=fail (180) header.d=sendgrid.me
Authentication-Results: mail.thetys-retz.net; dkim=pass (1024-bit key)
header.i=@sendgrid.me header.b=wKorgKG7; dkim-adsp=none
and yet none of them is displayed as dkim verified.
I'm using opendkim to sign and verify my emails.
By the way, email adress in the form of uid+id@domain.tld are valid !
Thanks